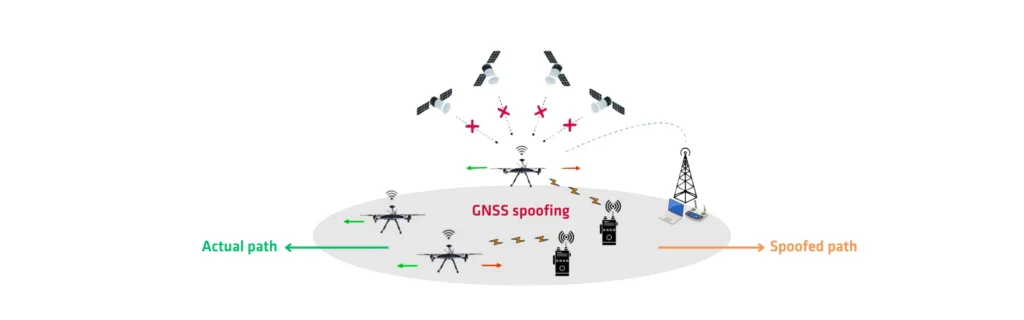
Spoofing mitigation refers to the strategies and technologies employed to protect Global Navigation Satellite Systems (GNSS) from spoofing attacks. Spoofing involves the transmission of false GNSS signals that mimic legitimate satellite signals, misleading receivers and potentially leading to incorrect positioning, navigation errors, or system manipulation. Effective spoofing mitigation is essential for safeguarding the integrity and reliability of GNSS services, which are critical for various applications including transportation, communications, and national security.
3 key aspects of spoofing mitigation:
1 – Identifying the presence of spoofing signals involves monitoring GNSS signal characteristics for inconsistencies or anomalies.
2 – Implementing measures to prevent spoofing attacks from affecting GNSS receivers.
3 – Taking corrective actions to address the impact of spoofing and restore accurate positioning and navigation.
Techniques for spoofing mitigation
Several techniques are utilized to mitigate the effects of spoofing on GNSS systems. These methods enhance the ability of GNSS receivers to discern between genuine and counterfeit signals.
1 – Signal authentication
Signal authentication techniques involve verifying the legitimacy of GNSS signals to ensure they are not spoofed.
Encrypted signals
Modern GNSS systems use encryption to protect the integrity of signals. Encrypted signals require a decryption key, which prevents unauthorized users from generating or interpreting false signals. This helps to ensure that only legitimate signals are processed by the receiver.
Authentication protocols
These protocols verify the authenticity of GNSS signals by checking their source and integrity. Any discrepancies or anomalies detected during this verification process can trigger alerts or initiate corrective measures.
2 – Multi-frequency and multi-constellation receivers
Multi-frequency and multi-constellation receivers enhance the capability of GNSS systems to detect and counteract spoofing attempts (spoofing mitigation).
Multi-frequency receivers
Receivers that process signals from multiple GNSS frequencies can cross-check signals to identify inconsistencies that may indicate spoofing. By analyzing data from different frequencies, these receivers can better distinguish genuine signals from spoofed ones.
Multi-constellation receivers
Additionally, these receivers can access signals from multiple GNSS constellations (such as GPS, GLONASS, Galileo, and Beidou). By comparing signals from various constellations, the receiver can detect anomalies and improve the accuracy and reliability of positioning data.
3 – Advanced signal processing techniques
Advanced signal processing Techniques improve the ability of GNSS receivers to detect and filter out spoofed signals.
Cross-correlation techniques
These techniques involve comparing the characteristics of received signals with known signal patterns. By identifying deviations from expected patterns, receivers can detect and filter out spoofed signals (spoofing mitigation).
Anomaly detection algorithms
These algorithms analyze GNSS signal data for unusual patterns or deviations. By identifying discrepancies from normal signal behavior, these algorithms can help detect spoofing attempts and reduce their impact.
4 – Detection and localization systems
Detection and localization systems are used to identify and locate sources of spoofing, enabling targeted responses.
Signal anomaly detection
Systems that monitor GNSS signals for irregularities can detect potential spoofing attacks. These systems provide alerts and support further investigation to confirm and address spoofing incidents.
Geolocation of spoofing sources
Techniques such as triangulation and direction finding can pinpoint the location of spoofing sources. By identifying the origin of spoofing signals, appropriate countermeasures can be implemented to mitigate their impact.
Importance of spoofing mitigation
Effective spoofing mitigation is critical for maintaining the reliability and accuracy of GNSS systems across various applications.
In safety-critical applications such as aviation, maritime navigation, and emergency services, accurate GNSS data plays a vital role in ensuring reliability and protecting human lives and valuable assets. Therefore, mitigating spoofing becomes essential to maintain the trustworthiness of navigation systems under all conditions. Moreover, many industries—including transportation, logistics, and land surveying—depend on precise positioning data to achieve operational efficiency. By implementing spoofing mitigation strategies, these sectors can preserve the integrity of their operations and avoid costly disruptions caused by misleading signals.
In addition to civilian and commercial applications, GNSS also underpins national defense and security missions. As a result, spoofing mitigation contributes directly to protecting critical infrastructure and maintaining the strategic effectiveness of military systems. Overall, across all these domains, the ability to detect and counter spoofing threats reinforces the safety, continuity, and resilience of modern navigation-dependent operations.
Spoofing mitigation is a crucial aspect of ensuring the accuracy and reliability of GNSS systems. By employing a combination of signal authentication techniques, advanced receivers, signal processing methods, and detection systems, it is possible to detect and counteract spoofing attacks effectively. As GNSS technology continues to evolve and its applications expand, ongoing efforts to enhance spoofing mitigation strategies will be essential for maintaining the security and functionality of global navigation and positioning services.