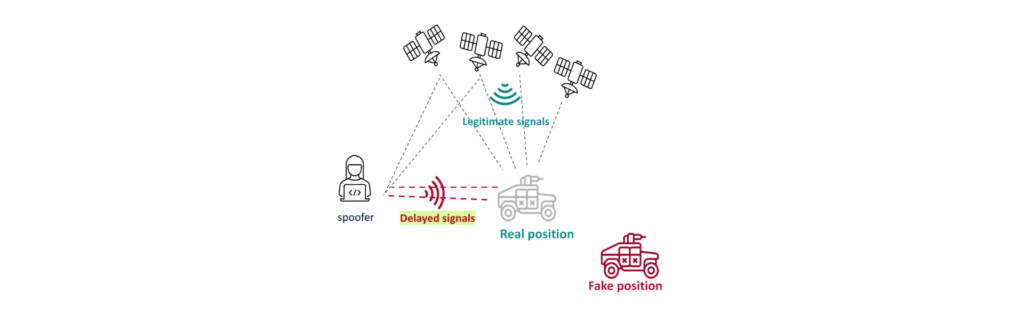
Spoofing refers to the deliberate broadcasting of false signals to deceive Global Navigation Satellite System (GNSS) receivers. Unlike jamming, which blocks GNSS signals altogether, spoofing tricks the receiver into calculating a false position, velocity, or time (PVT) solution. This deception can cause serious consequences in aviation, maritime navigation, autonomous vehicles, military operations, and critical infrastructure.
How spoofing works ?
Spoofers generate and transmit fake GNSS signals that closely resemble real satellite signals. These signals are often stronger than authentic ones, enabling the spoofed receiver to lock onto the counterfeit data. The attacker gradually overpowers the legitimate GNSS signals and shifts the calculated position or time, sometimes without the receiver detecting the change.
To carry out a successful spoofing attack, the adversary must synchronize with real satellite data, replicate signal structure, and then manipulate it in a way that appears seamless to the target system. Advanced spoofers use sophisticated signal generators capable of mimicking entire satellite constellations.
Detection Techniques
Several methods help detect GNSS spoofing:
- Signal strength analysis: Spoofed signals often exhibit abnormal power levels or sudden increases.
- Time-of-arrival inconsistencies: Receivers can identify discrepancies in the arrival times of satellite signals.
- Angle-of-arrival (AOA) detection: Antenna arrays detect unusual signal directions, revealing false sources.
- Multi-constellation and multi-frequency monitoring: Comparing multiple GNSS systems (GPS, Galileo, GLONASS) helps identify irregularities.
- Inertial Navigation System (INS) integration: INS provides position updates independent of GNSS, serving as a cross-check against spoofed data.
Spoofing countermeasures
To counter spoofing, system designers implement hardware and software-based approaches:
1 – Cryptographic GNSS signals: Modernized GNSS systems like Galileo (with OSNMA) and GPS (with M-code) offer authenticated signals, though not all civilian receivers support them yet.
2 – Receiver design improvements: Anti-spoofing algorithms compare signal parameters, timing, and direction to filter out malicious inputs.
3 – Sensor fusion: Combining GNSS with inertial sensors, barometers, magnetometers, and visual odometry makes spoofing less effective, as the navigation solution no longer relies solely on satellite signals.
Military-grade systems typically embed these capabilities, but they are becoming more common in commercial applications such as autonomous drones and shipping. The systems can be used to mitigate spoofing, meaconing or jamming.
What developments can we expect in the future ?
As navigation systems become increasingly autonomous and dependent on satellite signals, the risk of spoofing grows. Emerging sectors like autonomous cars, unmanned aerial vehicles (UAVs), and urban air mobility demand trustworthy navigation data. Governments and industries must adopt resilient navigation architectures that integrate multi-source verification, robust sensor fusion, and encrypted positioning data.
In conclusion, spoofing represents a silent, deceptive threat that can alter a system’s navigation data without raising alarms. By understanding how it operates, detecting its presence, and implementing robust countermeasures, engineers and operators can protect navigation systems and maintain trust in global mobility and positioning technologies.
Get ready for GNSS outages